To make our server running faster (Server Network Bandwidth Speed has been upgraded to 1 GBps(Gigabyte) / second),
more secure and confortable to use... (RAM has been Added with 16 gb too)
I've decided to use Apache with Light Speed PHP (lsphp) rather then features from CGI, FCGI, PHP-FPM and NGINX.
Since my server is using OS: The latest stable CloudLinux base kernel Server
Code: Select all
[root@srv8 ~]# hostnamectl
Static hostname: srv8.jsalfianmarketing.com
Icon name: computer-server
Chassis: server
Machine ID: bf4742a85c4148e08f755e4d7803f9c7
Boot ID: 6ee22a840e254d19be952e79964d4417
Operating System: CloudLinux 8.10 (Vladimir Aksyonov)
CPE OS Name: cpe:/o:cloudlinux:cloudlinux:8.10:GA:server
Kernel: Linux 4.18.0-553.22.1.lve.1.el8.x86_64
Architecture: x86-64
[root@srv8 ~]#For reference:
https://www.cloudlinux.com/getting-star ... iguration/
I've also configured Config Server Firewall (csf for DirectAdmin Panel Server) - Firewall module tools for every time login failure session attemp (LF_TRIGGER) from https://waytotheweb.com which is integrated with Directadmin Brute Force Monitoring Tools to the server for:
- login authenticator
- smtpauth
- dovecot
- lmtp
- pop3d
- sshd
- ftpd
- eximsyntax
- imapd
- Annoying mailicious massive exploit Scan Port activity
That's why we've been using JavaScript, TLS http:// rather than SSL https:// and you should allow to show images/pictures and white list our domains to get credits in all of our credit mailer links... and every time login failure session attempt (LF_TRIGGER) trigger to reach my server sources... the Firewall module will took the place...
This trick was used to trap all of the hackers and spammers, abuser that tried to use apps module: dovecot and pop3 to fetch the source of data from all of our mailer scripts...
For the reference:
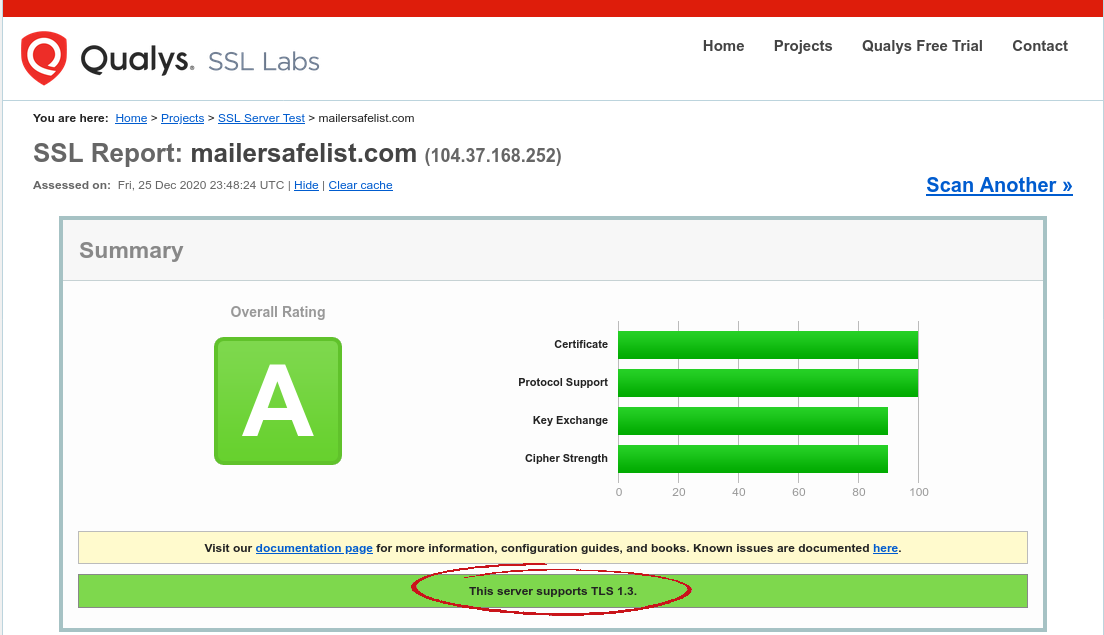
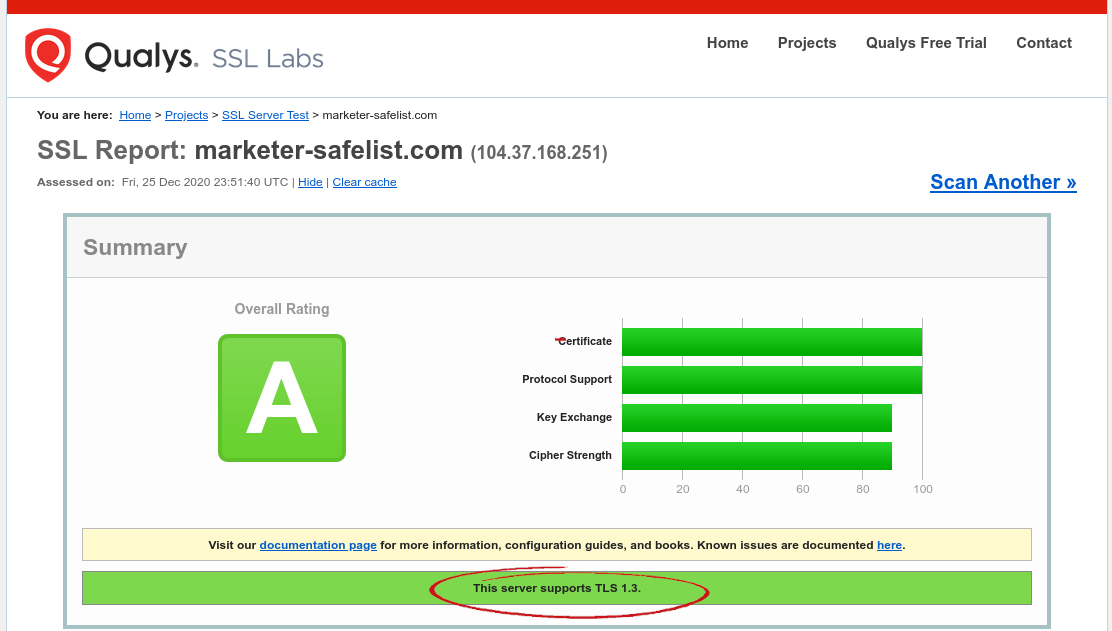
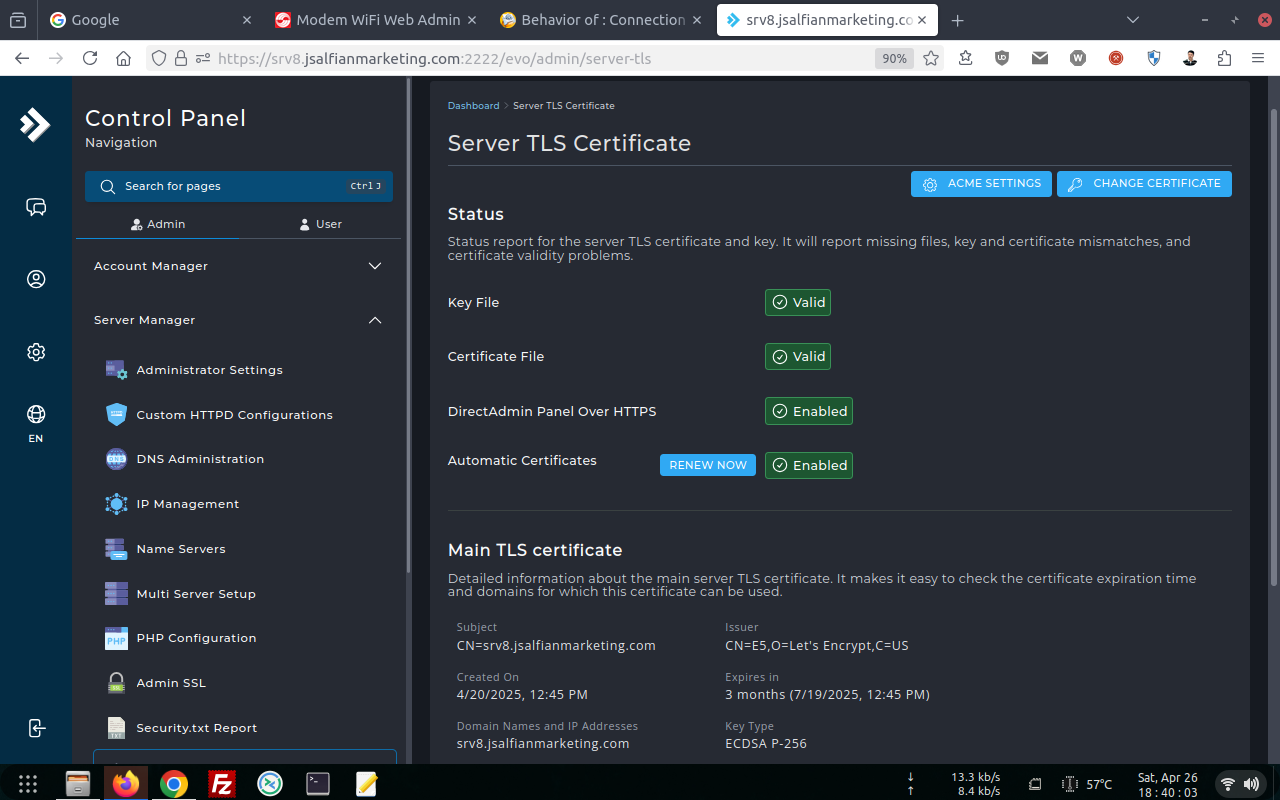
Have take a look!
Code: Select all
2024-11-08 16:01:02 cwd=/var/spool/exim 2 args: /usr/sbin/exim -q
2024-11-08 16:19:34 TLS error on connection from [27.147.153.138] (SSL_accept): (TLSv1)
2024-11-08 16:19:35 TLS error on connection from [176.241.89.210] (SSL_accept): (TLSv1)
2024-11-08 16:19:37 TLS error on connection from [209.203.63.8] (SSL_accept): (TLSv1)
...
...
2024-11-08 16:50:42 TLS error on connection from [41.215.28.234] (SSL_accept): (TLSv1)
2024-11-08 16:50:50 TLS error on connection from [41.84.141.86] (SSL_accept): (TLSv1)
2024-11-08 16:51:04 TLS error on connection from [41.215.28.234] (SSL_accept): (TLSv1)
...
...
2024-11-08 20:23:44 TLS error on connection from [139.59.152.85] (SSL_accept): (SSLv3)
2024-11-08 20:24:05 TLS error on connection from [139.59.159.80] SSL_accept: TCP connection closed by peer
...
...
2024-11-08 21:28:29 TLS error on connection from azpdesb64.stretchoid.com [4.156.21.164] (SSL_accept): (TLSv1.3)
2024-11-08 21:54:15 TLS error on connection from azpdsg45.stretchoid.com [172.202.158.131] (SSL_accept): (TLSv1.3)- MaxMind GeoIP Anonymous Proxies from : https://www.maxmind.com/en/anonymous_proxies
- BruteForceBlocker - Its main purpose is to block SSH bruteforce attacks https://danger.rulez.sk/index.php/bruteforceblocker/
- Stop Forum Spam from : http://www.stopforumspam.com/
- GreenSnow Hack List from : https://greensnow.co
- AbuseIPDB blacklist from : https://docs.abuseipdb.com/#blacklist-endpoint
- TOR Exit Nodes List from : https://trac.torproject.org/projects/to ... NSExitList
- HONEYPOT - identifying Dictionary Attacker IPs from : https://www.projecthoneypot.org
Code: Select all
May 16 15:38:21 srv8 lfd[1321179]: Retrieved and blocking blocklist GREENSNOW IP address ranges
May 16 15:38:22 srv8 lfd[1321179]: IPSET: loading set new_GREENSNOW with 3766 entries
May 16 15:38:22 srv8 lfd[1321179]: IPSET: switching set new_GREENSNOW to bl_GREENSNOW
May 16 15:38:22 srv8 lfd[1321179]: IPSET: loading set new_6_GREENSNOW with 0 entries
May 16 15:38:22 srv8 lfd[1321179]: IPSET: switching set new_6_GREENSNOW to bl_6_GREENSNOW
May 16 23:09:49 srv8 lfd[1486900]: Retrieved and blocking blocklist ABUSEIPDB IP address ranges
May 16 23:09:49 srv8 lfd[1486900]: IPSET: loading set new_ABUSEIPDB with 8652 entries
May 16 23:09:49 srv8 lfd[1486900]: IPSET: switching set new_ABUSEIPDB to bl_ABUSEIPDB
May 16 23:09:49 srv8 lfd[1486900]: IPSET: loading set new_6_ABUSEIPDB with 8 entries
May 16 23:09:49 srv8 lfd[1486900]: IPSET: switching set new_6_ABUSEIPDB to bl_6_ABUSEIPDB
Dec 18 06:59:02 srv8 lfd[787135]: Retrieved and blocking blocklist MAXMIND IP address ranges
Dec 18 06:59:02 srv8 lfd[787135]: IPSET: loading set new_MAXMIND with 324 entries
Dec 18 06:59:02 srv8 lfd[787135]: IPSET: switching set new_MAXMIND to bl_MAXMIND
Dec 18 06:59:02 srv8 lfd[787135]: IPSET: loading set new_6_MAXMIND with 0 entries
Dec 18 06:59:02 srv8 lfd[787135]: IPSET: switching set new_6_MAXMIND to bl_6_MAXMIND
May 16 23:24:52 srv8 lfd[1489798]: Retrieved and blocking blocklist STOPFORUMSPAM IP address ranges
May 16 23:24:52 srv8 lfd[1489798]: CC: Unzipped Blocklist STOPFORUMSPAM [/var/lib/csf/csf.block.STOPFORUMSPAM.zip]
May 16 23:24:52 srv8 lfd[1489798]: IPSET: loading set new_STOPFORUMSPAM with 3981 entries
May 16 23:24:52 srv8 lfd[1489798]: IPSET: switching set new_STOPFORUMSPAM to bl_STOPFORUMSPAM
Jun 2 21:15:04 srv8 lfd[3915398]: Retrieved and blocking blocklist BFB IP address ranges
Jun 2 21:15:04 srv8 lfd[3915398]: IPSET: loading set new_BFB with 241 entries
Jun 2 21:15:04 srv8 lfd[3915398]: IPSET: switching set new_BFB to bl_BFB
Jun 2 21:15:04 srv8 lfd[3915398]: IPSET: loading set new_6_BFB with 0 entries
Jun 2 21:15:04 srv8 lfd[3915398]: IPSET: switching set new_6_BFB to bl_6_BFB
Dec 18 04:37:43 srv8 lfd[702283]: Retrieved and blocking blocklist TOR IP address ranges
Dec 18 04:37:43 srv8 lfd[702283]: IPSET: loading set new_TOR with 738 entries
Dec 18 04:37:43 srv8 lfd[702283]: IPSET: switching set new_TOR to bl_TOR
Dec 18 04:37:43 srv8 lfd[702283]: IPSET: loading set new_6_TOR with 0 entries
Dec 18 04:37:43 srv8 lfd[702283]: IPSET: switching set new_6_TOR to bl_6_TOR
Dec 22 03:15:27 srv8 lfd[2362188]: Retrieved and blocking blocklist HONEYPOT IP address ranges
Dec 22 03:15:27 srv8 lfd[2362188]: IPSET: loading set new_HONEYPOT with 92 entries
Dec 22 03:15:27 srv8 lfd[2362188]: IPSET: switching set new_HONEYPOT to bl_HONEYPOT
Dec 22 03:15:27 srv8 lfd[2362188]: IPSET: loading set new_6_HONEYPOT with 8 entries
Dec 22 03:15:27 srv8 lfd[2362188]: IPSET: switching set new_6_HONEYPOT to bl_6_HONEYPOTmy server will blocking instantly all of the hackers, spammers, Scammers, malware and Spoofing/Phishing Attacks (Cybercriminals Attacker) from all over the world, that have been tried to attempt to reaching out our server with bad habit within seconds.
Have take a look:
Code: Select all
[root@srv8 ~]# tail -n 30 /var/log/lfd.log
Feb 8 00:00:03 srv8 lfd[1650618]: Directory Watching...
Feb 8 00:00:03 srv8 lfd[1650618]: Email Relay Tracking...
Feb 8 00:00:03 srv8 lfd[1650618]: Temp to Perm Block Tracking...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/www/html/phpMyAdmin/log/auth.log...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/log/customlog...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/log/exim/mainlog...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/log/directadmin/login.log...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/log/messages...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/www/html/squirrelmail/data/squirrelmail_access_log...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/log/maillog...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/www/html/roundcube/logs/errors.log...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/log/secure...
Feb 8 00:00:03 srv8 lfd[1650618]: Watching /var/log/httpd/error_log...
Feb 8 00:10:13 srv8 lfd[1652421]: (sshd) Failed SSH login from 129.146.162.206 (US/United States/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 00:28:10 srv8 lfd[1657434]: (smtpauth) Failed SMTP AUTH login from 124.136.29.20 (KR/South Korea/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 00:28:55 srv8 lfd[1657556]: (smtpauth) Failed SMTP AUTH login from 122.11.169.112 (SG/Singapore/122.11.169-112.unknown.starhub.net.sg): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 01:24:24 srv8 lfd[1666148]: (ftpd) Failed FTP login from 49.43.115.135 (IN/India/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 01:37:26 srv8 lfd[1668178]: (ftpd) Failed FTP login from 103.123.78.21 (IN/India/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 01:55:44 srv8 lfd[1670798]: (sshd) Failed SSH login from 34.170.15.98 (US/United States/98.15.170.34.bc.googleusercontent.com): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 02:12:22 srv8 lfd[1673501]: (smtpauth) Failed SMTP AUTH login from 12.207.244.211 (US/United States/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 02:12:38 srv8 lfd[1673554]: (smtpauth) Failed SMTP AUTH login from 222.179.102.210 (CN/China/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 02:14:23 srv8 lfd[1673802]: (smtpauth) Failed SMTP AUTH login from 102.165.14.139 (US/United States/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 02:32:52 srv8 lfd[1676620]: (eximsyntax) Exim syntax errors from 118.193.58.187 (DE/Germany/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 02:38:57 srv8 lfd[1677524]: (smtpauth) Failed SMTP AUTH login from 111.10.223.169 (CN/China/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 02:39:17 srv8 lfd[1677607]: (smtpauth) Failed SMTP AUTH login from 41.79.50.242 (GQ/Equatorial Guinea/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 04:07:28 srv8 lfd[1704294]: (smtpauth) Failed SMTP AUTH login from 102.165.14.140 (US/United States/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 04:37:44 srv8 lfd[1756825]: (sshd) Failed SSH login from 157.245.154.124 (SG/Singapore/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 04:54:17 srv8 lfd[1759242]: (smtpauth) Failed SMTP AUTH login from 27.72.155.221 (dynamic-adsl.viettel.vn): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 04:54:57 srv8 lfd[1759397]: (smtpauth) Failed SMTP AUTH login from 191.36.156.53 (BR/Brazil/vipturbo.com.br): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 04:55:07 srv8 lfd[1759506]: (sshd) Failed SSH login from 14.32.241.81 (KR/South Korea/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 06:02:21 srv8 lfd[1770132]: (sshd) Failed SSH login from 175.206.96.178 (KR/South Korea/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 06:14:26 srv8 lfd[1772079]: (smtpauth) Failed SMTP AUTH login from 23.95.86.94 (CA/Canada/solicitously.mutemeet.net): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 06:50:32 srv8 lfd[1777483]: (sshd) Failed SSH login from 222.111.179.159 (KR/South Korea/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 06:53:38 srv8 lfd[1777909]: (smtpauth) Failed SMTP AUTH login from 192.227.144.43 (US/United States/192-227-144-43-host.colocrossing.com): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 07:03:40 srv8 lfd[1779439]: (smtpauth) Failed SMTP AUTH login from 60.8.223.58 (CN/China/hebei.8.60.in-addr.arpa): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 07:04:00 srv8 lfd[1779512]: (smtpauth) Failed SMTP AUTH login from 120.193.223.46 (CN/China/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 07:05:55 srv8 lfd[1779858]: (ftpd) Failed FTP login from 103.26.81.177 (PK/Pakistan/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 07:28:08 srv8 lfd[1783286]: (sshd) Failed SSH login from 64.62.197.107 (US/United States/107.0-24.197.62.64.in-addr.arpa): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 07:43:46 srv8 lfd[1785558]: (smtpauth) Failed SMTP AUTH login from 191.36.152.28 (BR/Brazil/vipturbo.com.br): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 07:54:49 srv8 lfd[1834070]: (smtpauth) Failed SMTP AUTH login from 91.244.113.156 (RU/Russia/91.244.113.156.wirenet.tv): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 07:55:10 srv8 lfd[1835671]: (smtpauth) Failed SMTP AUTH login from 117.187.89.145 (CN/China/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 08:23:25 srv8 lfd[2029191]: (sshd) Failed SSH login from 64.62.197.127 (US/United States/127.0-24.197.62.64.in-addr.arpa): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 09:00:51 srv8 lfd[2047537]: (ftpd) Failed FTP login from 34.140.130.61 (BE/Belgium/61.130.140.34.bc.googleusercontent.com): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 09:01:57 srv8 lfd[2047700]: (ftpd) Failed FTP login from 35.190.199.12 (BE/Belgium/12.199.190.35.bc.googleusercontent.com): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 09:07:30 srv8 lfd[2048805]: (ftpd) Failed FTP login from 35.240.121.17 (BE/Belgium/17.121.240.35.bc.googleusercontent.com): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 09:17:15 srv8 lfd[2050301]: (sshd) Failed SSH login from 121.178.230.152 (KR/South Korea/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 09:23:56 srv8 lfd[2051263]: (sshd) Failed SSH login from 87.103.104.96 (PT/Portugal/96.104.103.87.rev.vodafone.pt): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 09:53:03 srv8 lfd[2090315]: (smtpauth) Failed SMTP AUTH login from 210.177.148.45 (HK/Hong Kong/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 09:53:33 srv8 lfd[2094714]: (smtpauth) Failed SMTP AUTH login from 210.18.182.188 (IN/India/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 09:54:18 srv8 lfd[2101298]: (ftpd) Failed FTP login from 165.154.163.113 (US/United States/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 10:18:42 srv8 lfd[2242935]: (smtpauth) Failed SMTP AUTH login from 188.32.109.40 (RU/Russia/broadband-188-32-109-40.ip.moscow.rt.ru): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 10:18:56 srv8 lfd[2244067]: (smtpauth) Failed SMTP AUTH login from 42.98.116.229 (HK/Hong Kong/42-98-116-229.static.netvigator.com): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 10:20:42 srv8 lfd[2252190]: (sshd) Failed SSH login from 64.62.197.211 (US/United States/211.0-24.197.62.64.in-addr.arpa): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 10:24:38 srv8 lfd[2269099]: (eximsyntax) Exim syntax errors from 58.48.226.61 (CN/China/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 10:24:38 srv8 lfd[2269100]: (eximsyntax) Exim syntax errors from 125.82.243.25 (CN/China/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 11:18:57 srv8 lfd[2280252]: (smtpauth) Failed SMTP AUTH login from 177.72.87.7 (BR/Brazil/7.lifedns.com.br): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 11:19:17 srv8 lfd[2280338]: (smtpauth) Failed SMTP AUTH login from 185.246.255.235 (IL/Israel/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 11:29:09 srv8 lfd[2281825]: (ftpd) Failed FTP login from 189.113.4.60 (BR/Brazil/sistemaev.com.br): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 11:43:49 srv8 lfd[2284011]: (ftpd) Failed FTP login from 31.148.250.165 (BY/Belarus/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Feb 8 12:01:00 srv8 lfd[2286671]: (ftpd) Failed FTP login from 185.203.236.130 (UZ/Uzbekistan/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
[root@srv8 ~]#For example: https://www.abuseipdb.com/check/87.64.71.57
For the reference: https://www.abuseipdb.com/csf
Such like these: (tail -F /var/log/lfd.log)
Code: Select all
Nov 16 05:14:11 srv8 lfd[286367]: (smtpauth) Failed SMTP AUTH login from 63.47.182.94 (US/United States/host94.sub-63-47-182.myvzw.com): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Nov 16 05:14:21 srv8 lfd[286389]: BLOCK_REPORT timed out after 10 seconds
Nov 16 05:14:51 srv8 lfd[286535]: (smtpauth) Failed SMTP AUTH login from 37.112.182.113 (RU/Russia/37x112x182x113.dynamic.barnaul.ertelecom.ru): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Nov 16 05:15:01 srv8 lfd[286557]: BLOCK_REPORT timed out after 10 seconds
Nov 16 05:21:52 srv8 lfd[288280]: (smtpauth) Failed SMTP AUTH login from 78.33.74.214 (GB/United Kingdom/78-33-74-214.static.enta.net): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Nov 16 05:22:02 srv8 lfd[288301]: BLOCK_REPORT timed out after 10 seconds
Nov 16 05:45:15 srv8 lfd[292572]: (sshd) Failed SSH login from 87.64.71.57 (BE/Belgium/57.71-64-87.adsl-dyn.isp.belgacom.be): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Nov 16 05:45:25 srv8 lfd[292594]: BLOCK_REPORT timed out after 10 seconds
Nov 16 06:01:08 srv8 lfd[295929]: (smtpauth) Failed SMTP AUTH login from 62.97.214.11 (NO/Norway/-): 1 in the last 3600 secs - *Blocked in csf* [LF_TRIGGER]
Nov 16 06:01:18 srv8 lfd[295950]: BLOCK_REPORT timed out after 10 secondsCode: Select all
[root@srv8 ~]# tail -n 30 /var/log/exim/rejectlog
2024-02-07 21:47:42 login authenticator failed for ([117.158.161.98]) [117.158.161.98]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-07 21:48:15 login authenticator failed for ([185.207.129.246]) [185.207.129.246]: 535 Incorrect authentication data (set_id=admin)
2024-02-07 21:55:37 login authenticator failed for (static.vnpt.vn) [113.160.203.147]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-07 21:55:51 login authenticator failed for (static.vnpt.vn) [113.175.240.142]: 535 Incorrect authentication data (set_id=admin)
2024-02-07 21:58:10 SMTP call from scan-54b.shadowserver.org [65.49.1.39] dropped: too many unrecognized commands (last was "Accept: */*")
2024-02-07 21:58:25 SMTP call from [65.49.1.62] dropped: too many unrecognized commands (last was "Accept: */*")
2024-02-07 22:32:23 login authenticator failed for ([183.215.1.244]) [183.215.1.244]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-07 22:32:39 login authenticator failed for ([196.20.104.226]) [196.20.104.226]: 535 Incorrect authentication data (set_id=admin)
2024-02-07 22:53:32 login authenticator failed for (192-3-198-20-host.colocrossing.com) [192.3.198.20]: 535 Incorrect authentication data (set_id=admin@marketer-safelist.com)
2024-02-08 00:28:06 login authenticator failed for ([114.53.252.254]) [124.136.29.20]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-08 00:28:50 login authenticator failed for (122.11.169-112.unknown.starhub.net.sg) [122.11.169.112]: 535 Incorrect authentication data (set_id=admin)
2024-02-08 00:58:03 SMTP call from scan-19.shadowserver.org [65.49.20.68] dropped: too many unrecognized commands (last was "Accept: */*")
2024-02-08 02:12:21 login authenticator failed for ([12.207.244.211]) [12.207.244.211]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-08 02:12:35 login authenticator failed for ([222.179.102.210]) [222.179.102.210]: 535 Incorrect authentication data (set_id=admin)
2024-02-08 02:14:21 login authenticator failed for (102.165.14.139) [102.165.14.139]: 535 Incorrect authentication data (set_id=admin@marketer-safelist.com)
2024-02-08 02:32:46 SMTP call from [118.193.58.187] dropped: too many syntax or protocol errors (last command was "?", NULL)
2024-02-08 02:38:52 login authenticator failed for ([111.10.223.169]) [111.10.223.169]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-08 02:39:15 login authenticator failed for ([41.79.50.242]) [41.79.50.242]: 535 Incorrect authentication data (set_id=admin)
2024-02-08 03:46:08 H=([128.65.164.36]) [128.65.164.36] F=<smtp_01@wikipedia.org> rejected RCPT <sales@lixinmetal.cn>: authentication required
2024-02-08 03:47:34 SMTP call from scan-59a.shadowserver.org [65.49.1.108] dropped: too many unrecognized commands (last was "Accept: */*")
2024-02-08 03:58:52 H=([128.65.164.36]) [128.65.164.36] F=<smtp_01@wikipedia.org> rejected RCPT <sales@lixinmetal.cn>: authentication required
2024-02-08 04:02:01 H=([128.65.164.36]) [128.65.164.36] F=<smtp_01@wikipedia.org> rejected RCPT <sales@lixinmetal.cn>: authentication required
2024-02-08 04:07:23 login authenticator failed for (localhost) [102.165.14.140]: 535 Incorrect authentication data (set_id=admin@marketer-safelist.com)
2024-02-08 04:26:09 H=([128.65.164.36]) [128.65.164.36] F=<smtp_01@wikipedia.org> rejected RCPT <sales@lixinmetal.cn>: authentication required
2024-02-08 04:52:56 H=([128.65.164.36]) [128.65.164.36] F=<smtp_01@wikipedia.org> rejected RCPT <sales@lixinmetal.cn>: authentication required
2024-02-08 04:54:15 login authenticator failed for (static.vnpt.vn) [27.72.155.221]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-08 04:54:52 login authenticator failed for (vipturbo.com.br) [191.36.156.53]: 535 Incorrect authentication data (set_id=admin)
2024-02-08 05:08:44 H=([128.65.164.36]) [128.65.164.36] F=<smtp_01@wikipedia.org> rejected RCPT <sales@lixinmetal.cn>: authentication required
2024-02-08 09:53:30 login authenticator failed for ([210.18.182.188]) [210.18.182.188]: 535 Incorrect authentication data (set_id=admin)
2024-02-08 10:18:38 login authenticator failed for broadband-188-32-109-40.ip.moscow.rt.ru [188.32.109.40]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-08 10:18:55 login authenticator failed for 42-98-116-229.static.netvigator.com [42.98.116.229]: 535 Incorrect authentication data (set_id=admin)
2024-02-08 10:24:34 SMTP call from [58.48.226.61] dropped: too many syntax or protocol errors (last command was "?", NULL)
2024-02-08 10:24:36 SMTP call from [125.82.243.25] dropped: too many syntax or protocol errors (last command was "?", NULL)
2024-02-08 10:24:37 SMTP call from [112.94.253.241] dropped: too many unrecognized commands (last was "")
2024-02-08 11:18:53 login authenticator failed for (7.lifedns.com.br) [177.72.87.7]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-08 11:19:13 login authenticator failed for ([185.246.255.235]) [185.246.255.235]: 535 Incorrect authentication data (set_id=admin)
2024-02-08 12:12:07 login authenticator failed for (static.vnpt.vn) [113.161.40.240]: 535 Incorrect authentication data (set_id=admin@mailersafelist.com)
2024-02-08 12:13:18 login authenticator failed for (71.58.221.60.adsl-pool.sx.cn) [60.221.58.71]: 535 Incorrect authentication data (set_id=admin)
2024-12-07 13:43:39 H=([213.230.87.190]) [213.230.87.190] F=<JohnBlue@hola.com> rejected RCPT <admin@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2024-12-07 15:30:25 H=(habitatwarm.best) [194.1.192.3] F=<contact@habitatwarm.best> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2024-12-07 16:42:35 H=(privilegeflimsy.best) [194.1.192.13] F=<memorybreakthrough@privilegeflimsy.best> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2024-12-17 10:50:05 H=(dr3qm.cn) [165.154.205.177] X=TLS1.2:ECDHE-ECDSA-AES128-GCM-SHA256:128 CV=no F=<faq.mizuhobank.co.jp1@dr3qm.cn> rejected RCPT <admin@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2024-12-18 11:11:02 H=optimaltherapies.best [51.158.20.224] F=<powerperformance@optimaltherapies.best> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2024-12-18 11:22:05 H=mout-xforward.gmx.net [82.165.159.14] X=TLS1.3:TLS_AES_256_GCM_SHA384:256 CV=no F=<cyndyjusto1998@gmx.us> rejected RCPT <admin@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2024-12-18 12:11:53 H=integrativealliance.best [51.158.44.20] F=<support@integrativealliance.best> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2024-12-18 16:03:49 H=1-tor-exit.spooky69.eu (localhost) [193.218.118.91] F=<test1@funteensex.com> rejected RCPT <vgarcia@marketer-safelist.com>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-01-21 04:42:48 H=(quicktoday.za.com) [192.3.223.164] F=<info@quicktoday.za.com> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2025-01-21 05:41:08 H=(smarthealth.sa.com) [192.3.223.165] F=<info@smarthealth.sa.com> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2025-01-21 08:29:42 H=(focusguide.za.com) [192.3.223.167] F=<info@focusguide.za.com> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2025-01-21 20:06:47 H=zara.probe.onyphe.net (104.37.168.248) [15.235.189.144] rejected EHLO or HELO 104.37.168.248: HELO is an IP address (See RFC2821 4.1.3)
2025-01-21 21:41:20 H=([51.15.184.73]) [92.126.223.175] F=<6yv7joipexvy7@longdotech.com> rejected RCPT <postmaster@jsalfianmarketing.com>: Email blocked by b.barracudacentral.org (127.0.0.2)
2025-01-21 21:41:20 H=([51.15.184.73]) [92.126.223.175] F=<6yv7joipexvy7@longdotech.com> rejected RCPT <abuse@jsalfianmarketing.com>: Email blocked by b.barracudacentral.org (127.0.0.2)
2025-01-21 21:44:20 H=([51.15.184.101]) [185.101.16.250] F=<c398tx0kd7v402@remyra.no> rejected RCPT <postmaster@jsalfianmarketing.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2025-01-21 21:44:20 H=([51.15.184.101]) [185.101.16.250] F=<c398tx0kd7v402@remyra.no> rejected RCPT <abuse@jsalfianmarketing.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2025-09-20 12:09:47 H=(qyw.blog) [197.255.204.240] X=TLS1.3:TLS_AES_256_GCM_SHA384:256 CV=no F=<rodos18048@igoqu.com> rejected RCPT <admin@marketer-safelist.com>: Email blocked by b.barracudacentral.org (127.0.0.2)
2025-09-20 15:17:40 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 15:28:28 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 15:49:37 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 15:51:17 H=(WIN-7N1FIECL6IC) [158.94.208.119] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 15:51:17 H=(WIN-7N1FIECL6IC) [158.94.208.119] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 15:51:17 H=(WIN-7N1FIECL6IC) [158.94.208.119] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 15:51:17 H=(WIN-7N1FIECL6IC) [158.94.208.119] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 15:51:18 H=(WIN-7N1FIECL6IC) [158.94.208.119] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 15:51:18 H=(WIN-7N1FIECL6IC) [158.94.208.119] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 15:51:49 rejected EHLO from o67.scanner.modat.io [51.161.174.170]: syntactically invalid argument(s): (no argument given)
2025-09-20 16:15:59 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 16:48:33 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 17:08:55 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 17:25:05 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 17:40:18 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 18:09:05 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 18:14:58 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 18:19:30 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 18:30:32 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 19:09:21 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 19:42:53 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 19:57:48 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 20:04:47 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 20:32:42 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 20:40:14 H=([213.209.157.137]) [213.209.157.137] rejected MAIL <dpr@priv8shop.com>: authentication required
2025-09-20 21:19:18 H=(WIN-7N1FIECL6IC) [178.16.54.138] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 21:19:18 H=(WIN-7N1FIECL6IC) [178.16.54.138] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 21:19:18 H=(WIN-7N1FIECL6IC) [178.16.54.138] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 21:19:18 H=(WIN-7N1FIECL6IC) [178.16.54.138] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 21:19:18 H=(WIN-7N1FIECL6IC) [178.16.54.138] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 21:19:20 H=(WIN-7N1FIECL6IC) [178.16.54.138] F=<spameri@tiscali.it> rejected RCPT <spameri@tiscali.it>: R1: HELO should be a FQDN or address literal (See RFC 2821 4.1.1.1)
2025-09-20 21:37:43 H=(gadgetkingdommy.za.com) [23.228.85.158] F=<gadgetronixs@gadgetkingdommy.za.com> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
2025-09-20 22:48:59 H=(gotechworld.sa.com) [23.228.85.159] F=<jetfan@gotechworld.sa.com> rejected RCPT <jerry.salfian@marketer-safelist.com>: 554 denied. 5.7.1 Domain Blocked due to SPAM
[root@srv8 ~]#Code: Select all
AR, BD, BE, BR, CN, GH, HK, IN, IQ, IR, KR, LT, NO, PK, TH, TW, VN, RO, RU, SE, ZW, AS749, AS2639, AS6939, AS8075, AS8560, AS9009, AS10439, AS14061, AS14618, AS14987, AS16509, AS20473, AS23033, AS24940, AS26548, AS28753, AS36352, AS36937, AS42624, AS45102, AS47890, AS51159, AS63949, AS132203, AS135377, AS136907, AS139341, AS142002, AS199654, AS202306, AS202425, AS208843, AS209605, AS209800, AS210558, AS211298, AS212027, AS213186, AS213230, AS213790, AS214295, AS214940, AS214943, AS215476, AS215930, AS216383, AS396982, AS398722, AS401109and also... Regarding CSF Firewall configuratiion for the CC_DENY and ASN (hosting company)... Dont forget to check your Repo Mirror List connection for your server such like this:
Code: Select all
[root@srv8 ~]# ping -c 5 repo.cloudlinux.com
PING repo.cloudlinux.com (178.156.194.6) 56(84) bytes of data.
64 bytes from static.6.194.156.178.clients.your-server.de (178.156.194.6): icmp_seq=1 ttl=45 time=70.5 ms
64 bytes from static.6.194.156.178.clients.your-server.de (178.156.194.6): icmp_seq=2 ttl=45 time=68.8 ms
64 bytes from static.6.194.156.178.clients.your-server.de (178.156.194.6): icmp_seq=3 ttl=45 time=68.8 ms
64 bytes from static.6.194.156.178.clients.your-server.de (178.156.194.6): icmp_seq=4 ttl=45 time=68.8 ms
64 bytes from static.6.194.156.178.clients.your-server.de (178.156.194.6): icmp_seq=5 ttl=45 time=68.8 ms
--- repo.cloudlinux.com ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4007ms
rtt min/avg/max/mdev = 68.778/69.134/70.500/0.683 ms
[root@srv8 ~]# yum update --disablerepo=appstream,baseos,powertools
This system is receiving updates from CloudLinux Network server.
CloudLinux-8 - Gradual Rollout Slot 1 9.1 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 2 45 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 3 49 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 4 9.2 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 5 50 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 6 9.2 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 7 51 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 8 2.4 kB/s | 3.0 kB 00:01
CloudLinux-8 - Gradual Rollout Slot 9 9.2 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 10 38 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 11 602 B/s | 3.0 kB 00:05
CloudLinux-8 - Gradual Rollout Slot 12 9.2 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 13 51 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 14 9.2 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 14 158 B/s | 257 B 00:01
CloudLinux-8 - Gradual Rollout Slot 15 4.8 kB/s | 3.0 kB 00:00
CloudLinux-8 - Gradual Rollout Slot 16 9.1 kB/s | 3.0 kB 00:00
Extra Packages for Enterprise Linux 8 - x86_64 390 kB/s | 34 kB 00:00
Extra Packages for Enterprise Linux 8 - x86_64 3.3 MB/s | 14 MB 00:04
Dependencies resolved.
Nothing to do.
Complete!
[root@srv8 ~]#Code: Select all
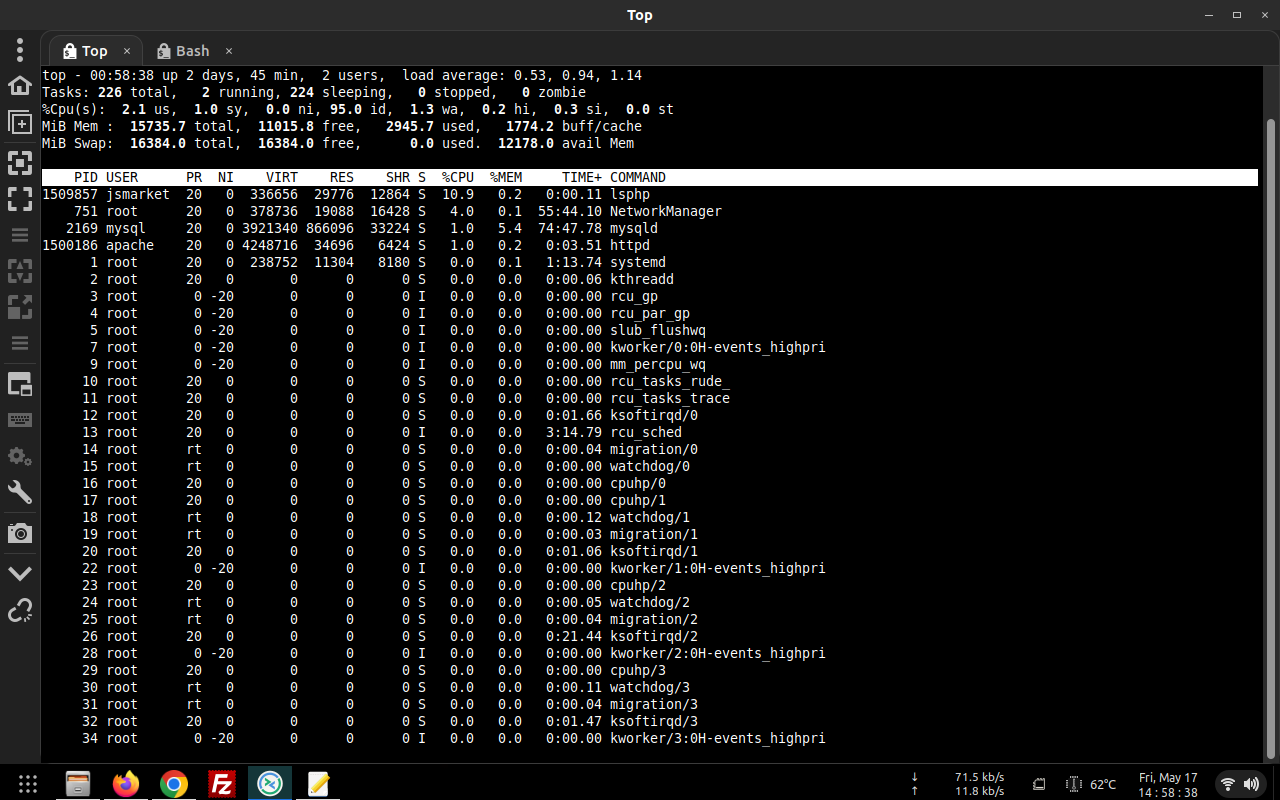
top - 23:39:34 up 3 days, 17:12, 2 users, load average: 0.25, 0.48, 0.57
Tasks: 225 total, 1 running, 224 sleeping, 0 stopped, 0 zombie
%Cpu(s): 0.2 us, 0.5 sy, 0.2 ni, 99.0 id, 0.0 wa, 0.2 hi, 0.0 si, 0.0 stCustomBuild permissions for these service modules have been granted:
Code: Select all
[root@srv8 ~]# ls -la /var/spool/exim/
total 4
drwxr-x--- 6 mail mail 120 Feb 6 18:57 .
drwxr-xr-x. 11 root root 4096 Feb 6 13:09 ..
drwxr-x--- 2 mail mail 160 Feb 6 18:57 db
drwxr-x--- 64 mail mail 1280 Feb 6 18:00 input
drwxr-x--- 64 mail mail 1280 Feb 6 18:00 msglog
drwxr-x--- 2 mail mail 40 Feb 8 03:05 scan
[root@srv8 ~]#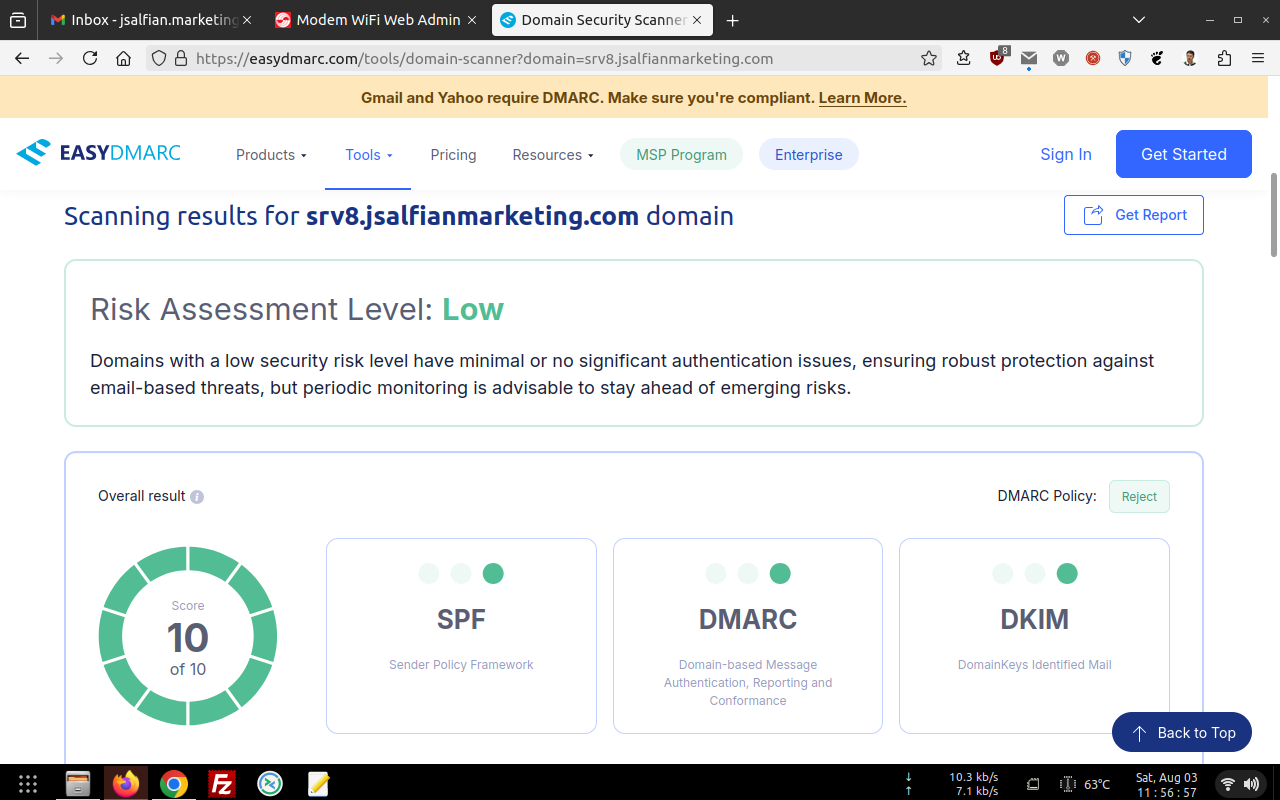
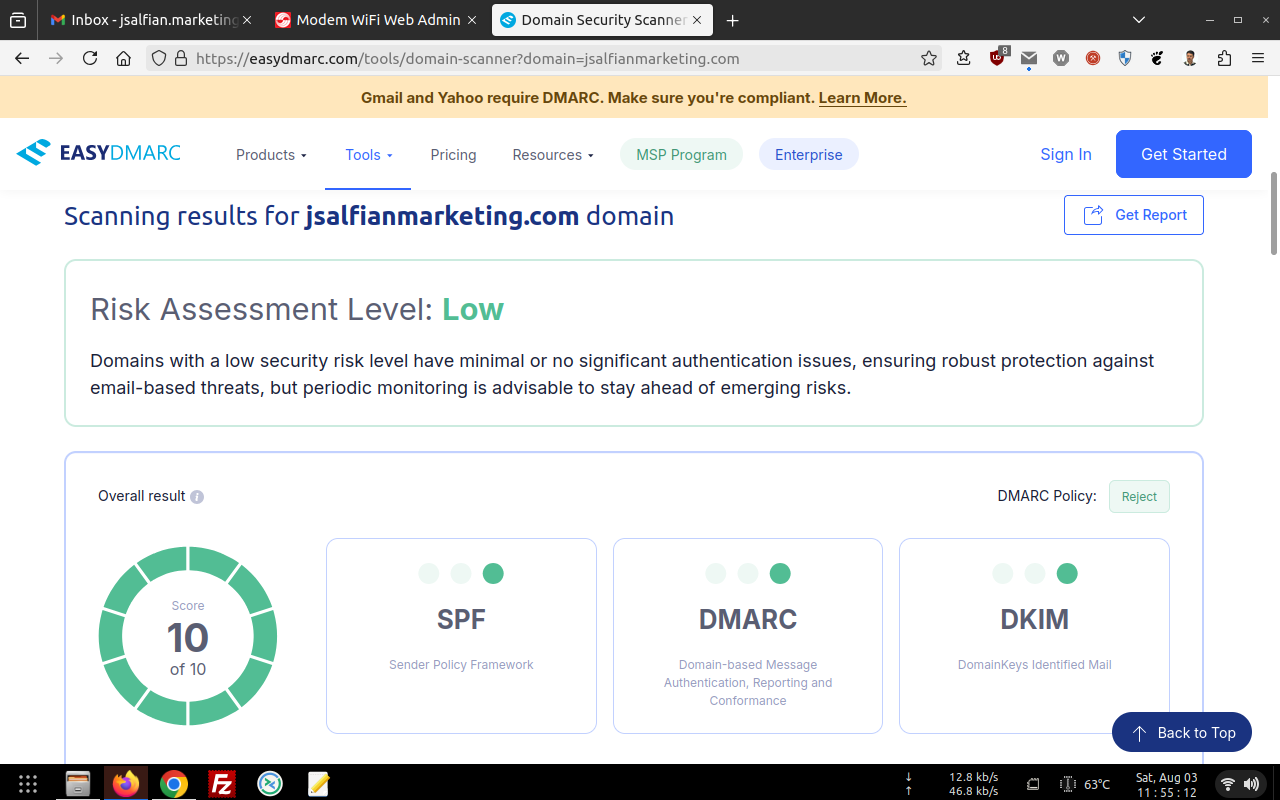
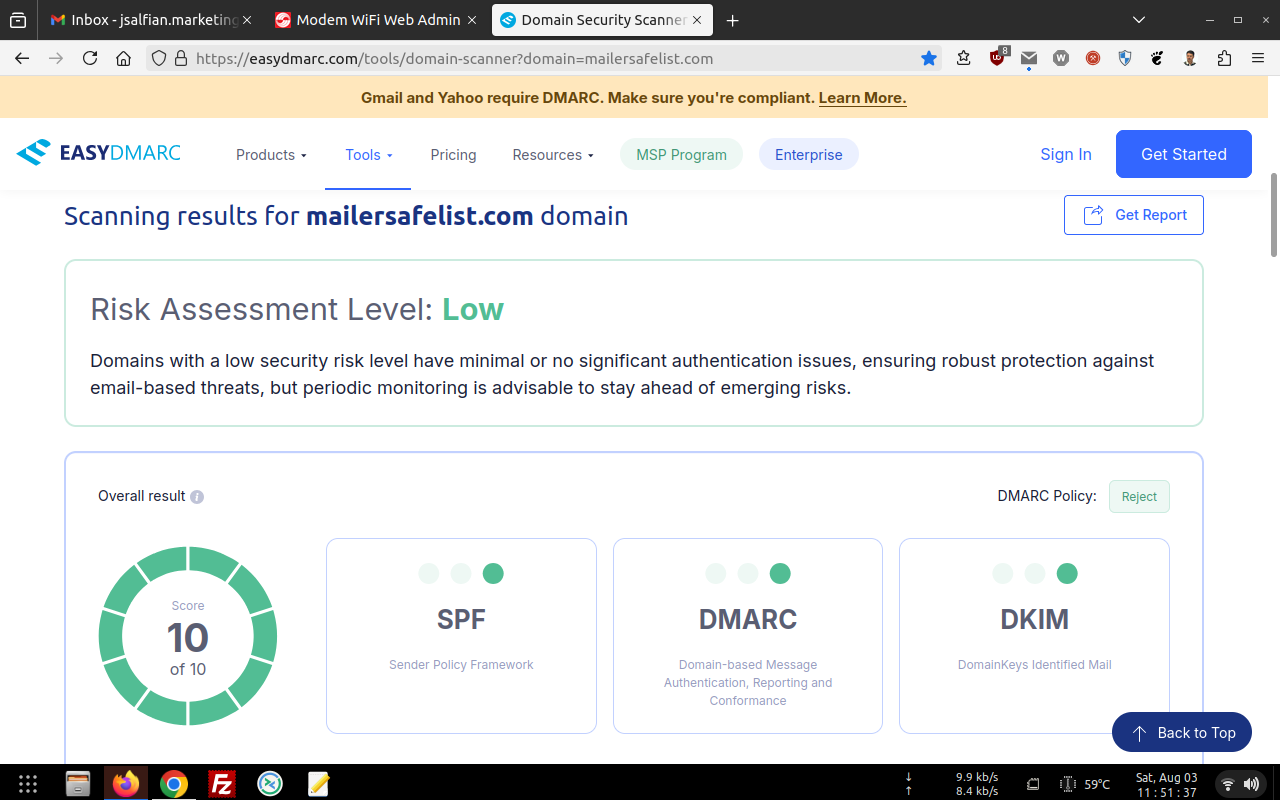
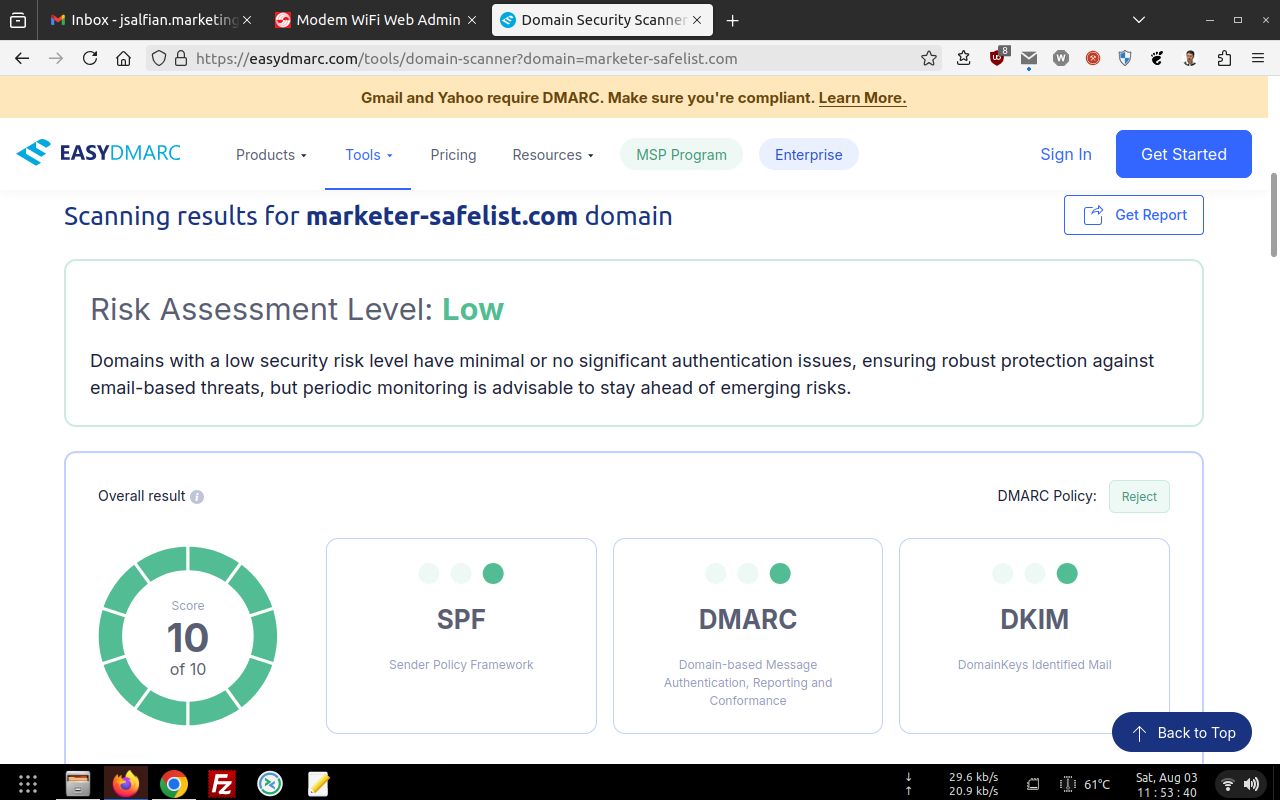
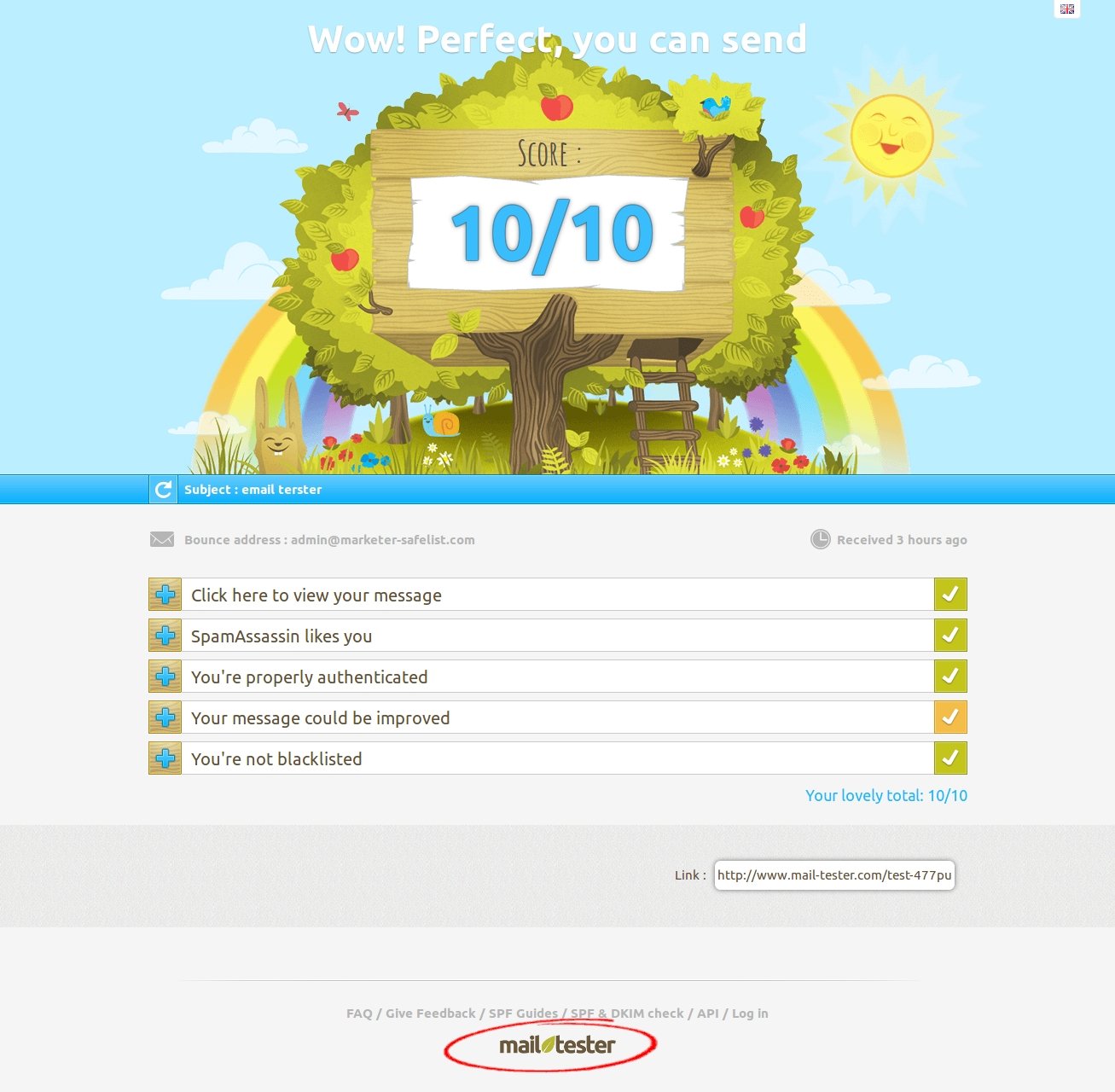
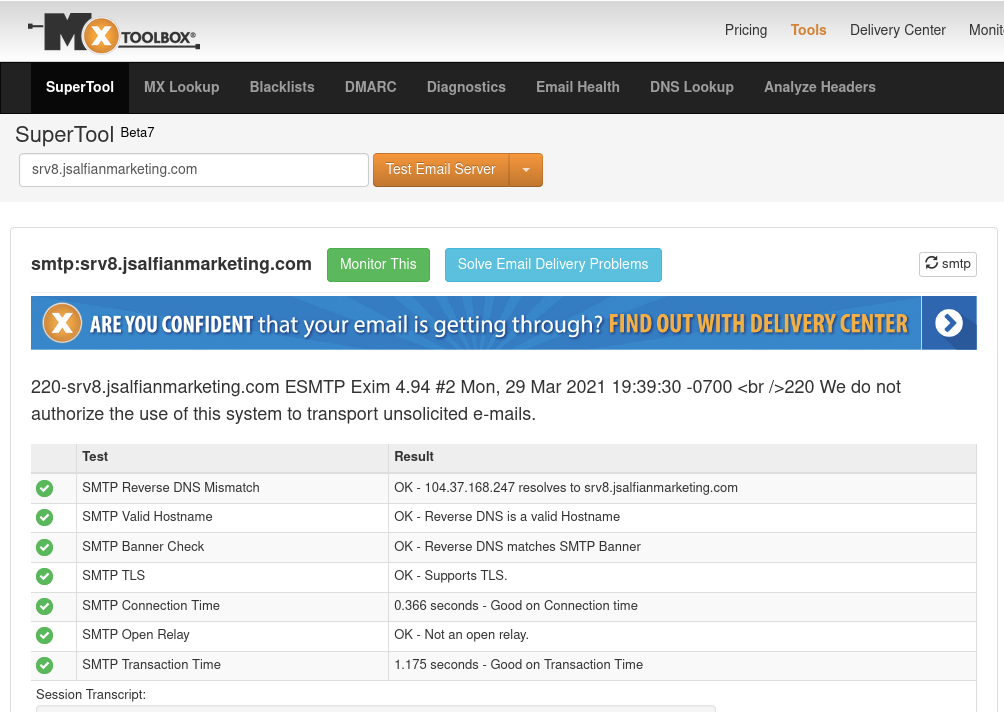
Regularly... have been already checked within 103 RBL's and Gmail Postmaster Compliance tools too !!!
For RBL's screenshot... You might need to open these images below in the new tab for sure, Then pointing your cursor to the image you've choosen, right click the image to get the direction option (Firefox and Google Chrome Browser) and choose "open the image in the new tab", lastly... "click the image to maximize".
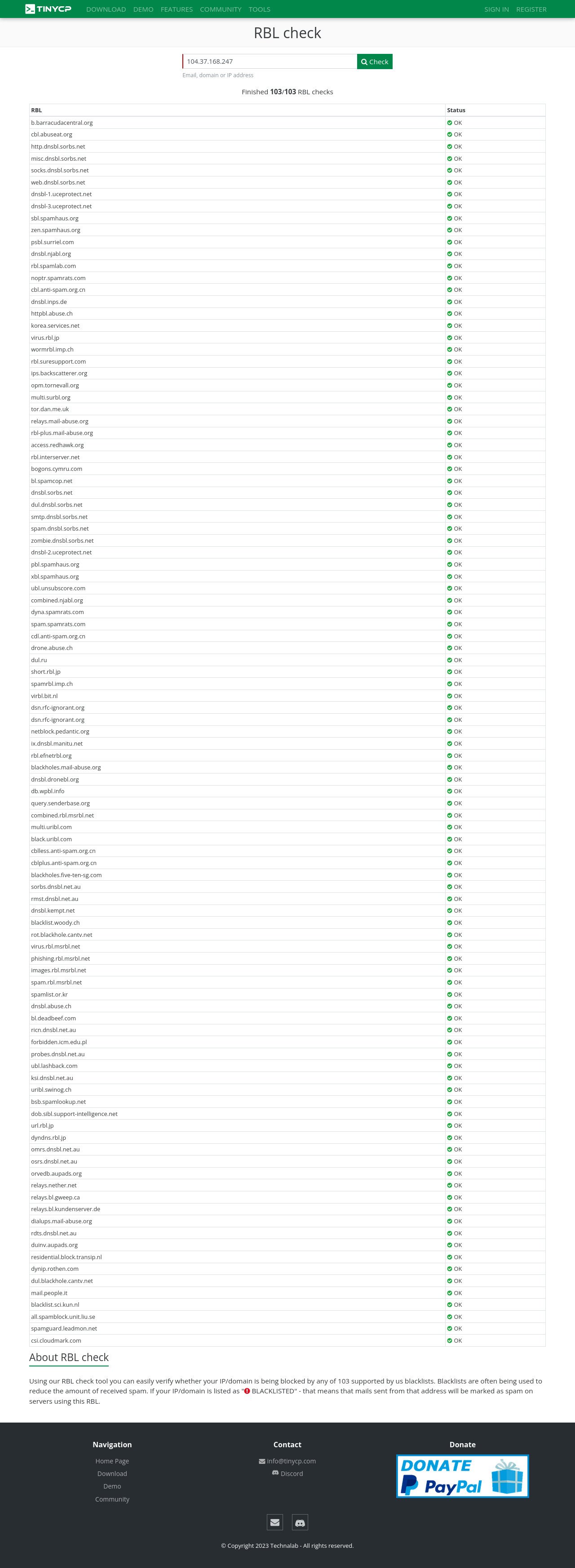
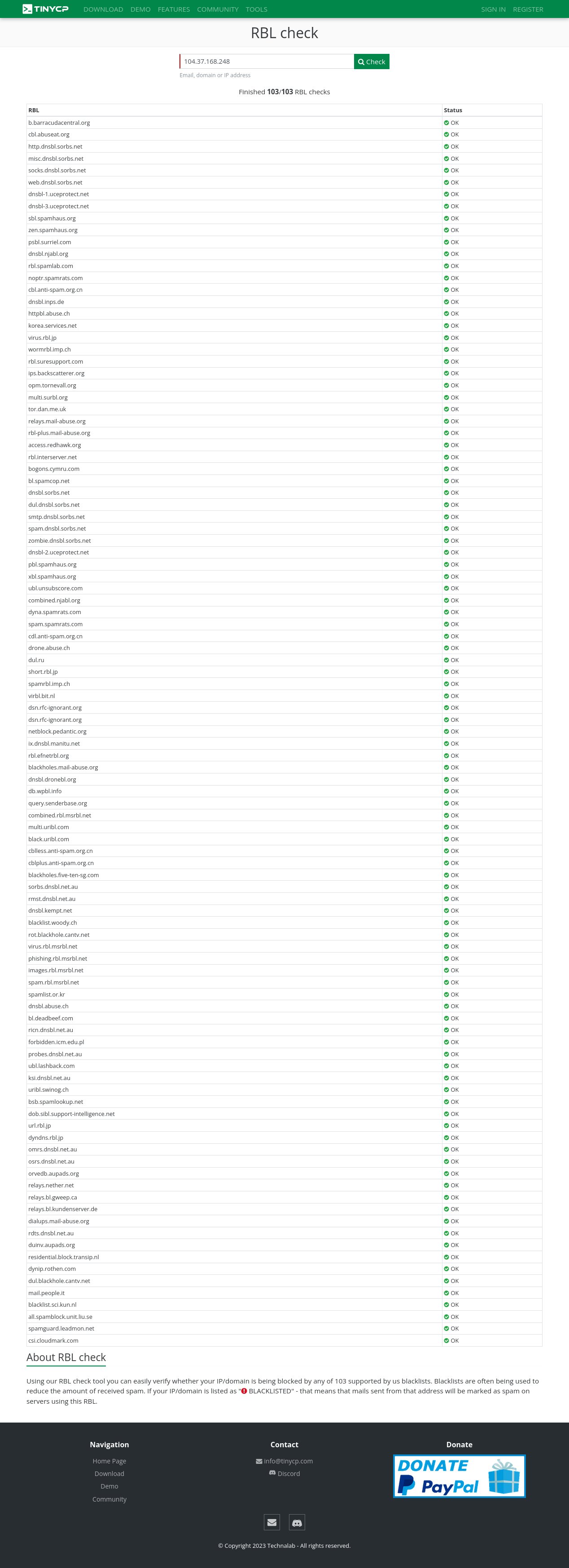
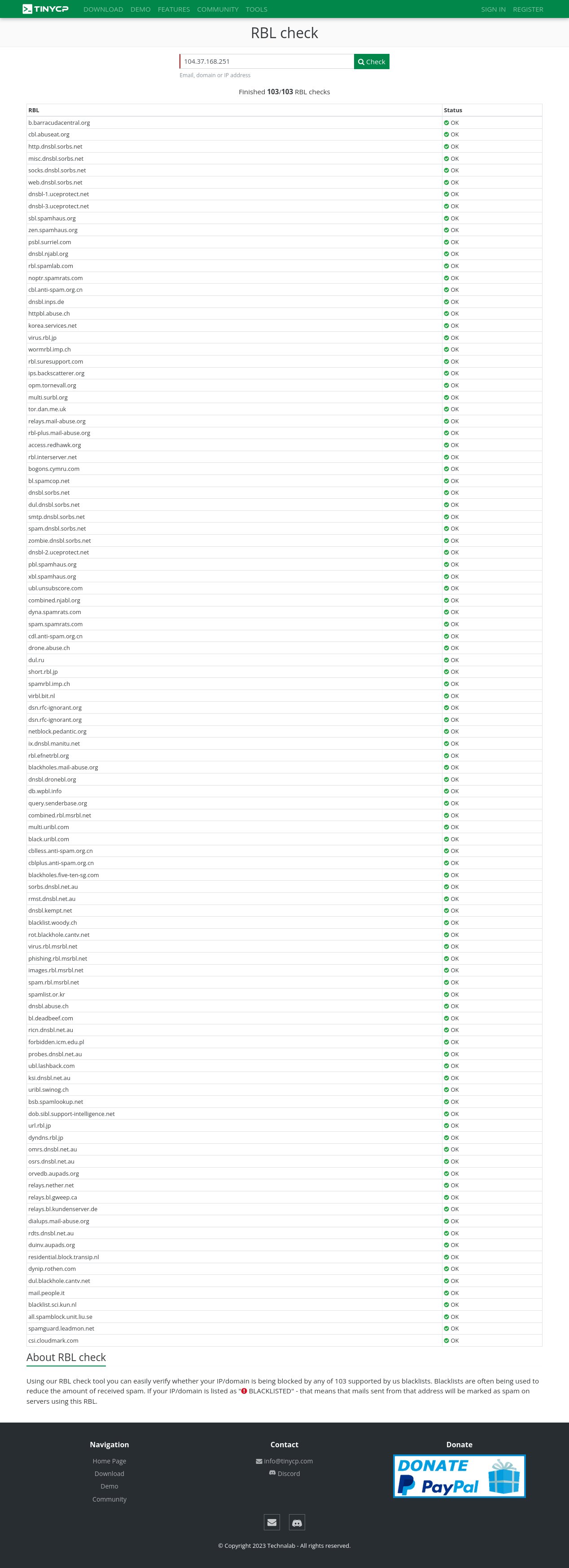
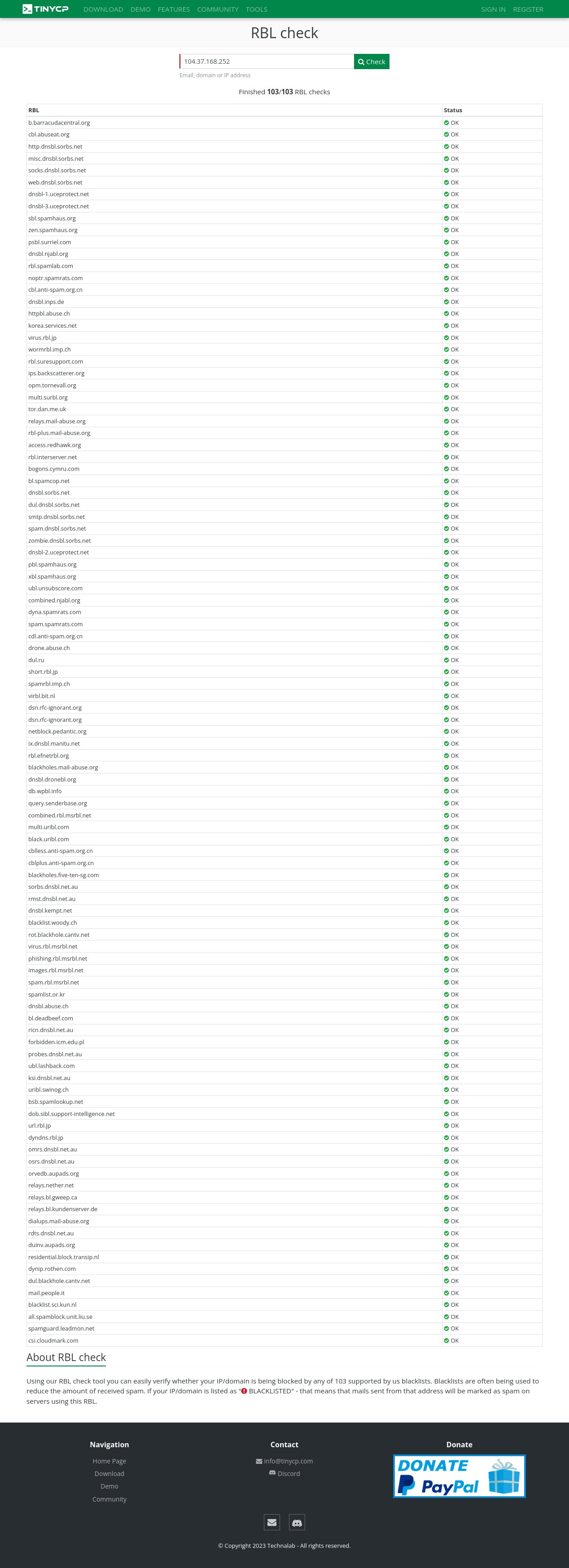



More security improvement will be added in the next future development.