To get more secure, stable and faster mail server on Exim configuration tweaks... and to get rid out from these:
Spammers, Abusers, Phishing attack...
and for the mitigation purpose, I've already blocked or rejected Dovecot connection Authentication process failure, TLS error on connection, SMTP error connection with TCP/IP call and inbound emails from all over the world:
Blocked Countries
Your server rejects mail that originates from these countries. (A new browser tab will appear.)
except from :
Trusted legal mail user
Users on the system that may set the From: header to anything they like when "Rewrite From: header to match actual sender" is enabled.
Trusted IP's Address
IP addresses exempt from all SMTP sender, recipient, spam, and relaying checks. IP addresses you enter here are stored in /etc/skipsmtpcheckhosts.
These senders must still use an RFC-compliant HELO name if the Require RFC-compliant HELO setting is enabled.
within WHM:
Home /Service Configuration /Exim Configuration Manager/ Basic Editor Tab /Access List
Now my mail server running excellent using CSF-firewall, compiled with sleek WHM exim configuration tweaks!
Code: Select all
[root@srv8 ~]# hostnamectl
Static hostname: srv8.jsalfianmarketing.com
Icon name: computer-desktop
Chassis: desktop
Machine ID: 9d9843c00baa42cfb6faxxxf725cdc5e
Boot ID: 9281xxx105a7437481b96a640749090f
Operating System: CloudLinux 7.9 (Boris Yegorov)
CPE OS Name: cpe:/o:cloudlinux:cloudlinux:7.9:GA:server
Kernel: Linux 3.10.0-962.3.2.lve1.5.73.el7.x86_64
Architecture: x86-64
[root@srv8 ~]# cat /usr/local/cpanel/version
11.102.0.23
[root@srv8 ~]#
Checked within 103 RBL's
(You might need to open this image in the new tab for sure)
(Pointing you cursor tho the image below, right click the image option, and choose open the image in the new tab, click the image to maximize)
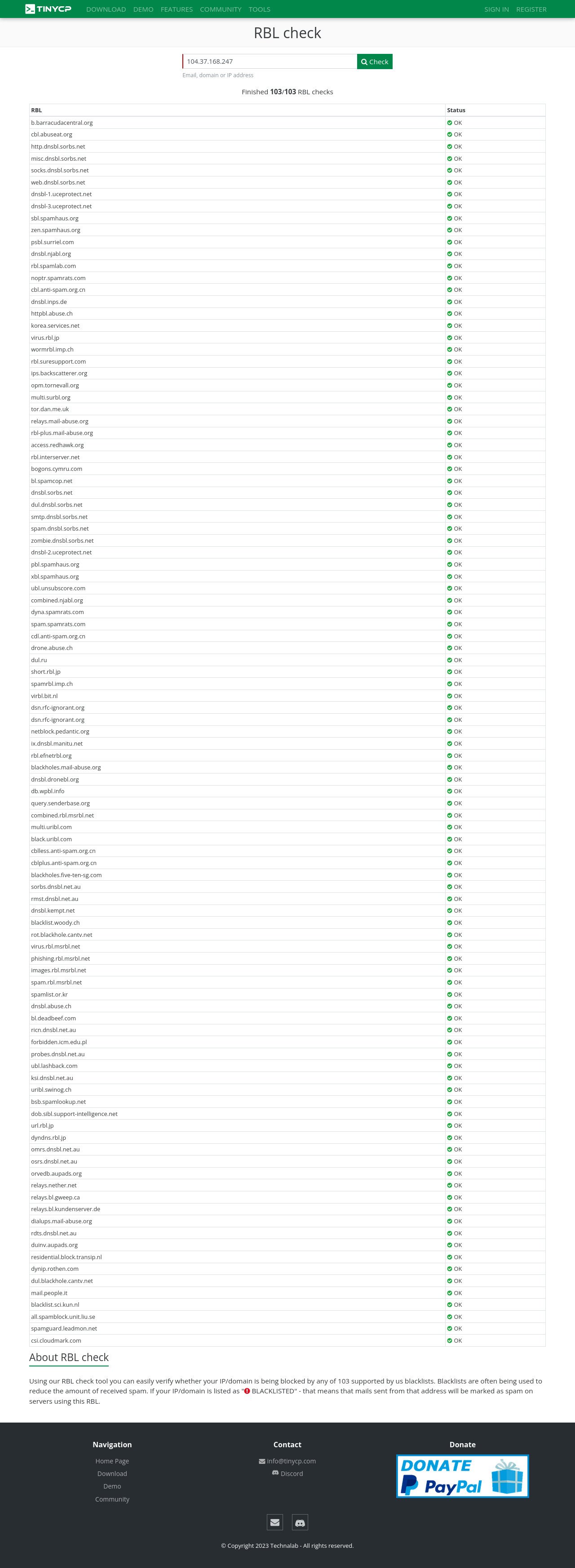
Displaying of /var/log/exim_mainlog:
Say goodbye to all of Spammers, Abusers, Phishing attacker... FOREVER!
Code: Select all
2022-10-05 20:50:54 SMTP connection from [52.52.26.65]:54284 (TCP/IP connection count = 1)
2022-10-05 20:51:35 H=ca1.mx-check.com (mx-check.com) [52.52.26.65]:54284 X=TLS1.2:ECDHE-RSA-AES256-GCM-SHA384:256 CV=no F= temporarily rejected RCPT : Deferred due to greylisting. Host: '52.52.26.65' From: 'check@mx-check.com' To: 'postmaster@business-mailers.com' SPF: 'unchecked'
2022-10-05 20:52:37 cwd=/etc/csf 2 args: /usr/sbin/exim -bpc
2022-10-05 20:53:31 unexpected disconnection while reading SMTP command from ca1.mx-check.com (mx-check.com) [52.52.26.65]:54284 D=2m36s
2022-10-05 20:54:16 cwd=/var/spool/exim 2 args: /usr/sbin/exim -q
2022-10-05 21:04:00 SMTP connection from [162.142.125.10]:36772 (TCP/IP connection count = 1)
2022-10-05 21:04:02 SMTP connection from [177.174.0.133]:33080 (TCP/IP connection count = 2)
2022-10-05 21:04:04 H=[177.174.0.133]:33080 X=TLS1.2:ECDHE-RSA-AES256-GCM-SHA384:256 CV=no rejected connection in "connect" ACL: Country is banned
2022-10-05 21:04:04 SMTP connection from [177.174.0.133]:33080 closed by DROP in ACL
2022-10-05 21:04:22 H=scanner-04.ch1.censys-scanner.com [162.142.125.10]:36772 rejected connection in "connect" ACL: Host is banned
2022-10-05 21:04:22 SMTP connection from scanner-04.ch1.censys-scanner.com [162.142.125.10]:36772 closed by DROP in ACL
2022-10-05 21:05:19 SMTP connection from [43.131.49.100]:49656 (TCP/IP connection count = 1)
2022-10-05 21:05:19 H=[43.131.49.100]:49656 rejected connection in "connect" ACL: Country is banned
2022-10-05 21:05:19 SMTP connection from [43.131.49.100]:49656 closed by DROP in ACL
2022-10-05 21:05:19 no host name found for IP address 43.131.49.100
2022-10-05 21:07:08 SMTP connection from [45.83.65.96]:30546 (TCP/IP connection count = 1)
2022-10-05 21:07:09 H=[45.83.65.96]:30546 X=TLS1.2:ECDHE-RSA-AES128-GCM-SHA256:128 CV=no rejected connection in "connect" ACL: Country is banned
2022-10-05 21:07:09 SMTP connection from [45.83.65.96]:30546 closed by DROP in ACL
2022-10-05 21:07:09 no host name found for IP address 45.83.65.96
2022-10-05 21:07:39 cwd=/etc/csf 2 args: /usr/sbin/exim -bpc
2022-10-05 21:09:01 SMTP connection from [45.83.64.220]:23588 (TCP/IP connection count = 1)
2022-10-05 21:09:01 H=[45.83.64.220]:23588 X=TLS1.2:ECDHE-RSA-AES128-GCM-SHA256:128 CV=no rejected connection in "connect" ACL: Country is banned
2022-10-05 21:09:01 SMTP connection from [45.83.64.220]:23588 closed by DROP in ACL
2022-10-05 21:09:01 no host name found for IP address 45.83.64.220
2022-10-05 21:11:14 SMTP connection from [87.236.176.233]:34209 (TCP/IP connection count = 1)
2022-10-05 21:11:14 H=[87.236.176.233]:34209 rejected connection in "connect" ACL: Country is banned
2022-10-05 21:11:14 SMTP connection from [87.236.176.233]:34209 closed by DROP in ACL
2022-10-05 21:11:16 SMTP connection from [104.248.203.191]:54131 (TCP/IP connection count = 1)
2022-10-05 21:11:16 H=[104.248.203.191]:54131 rejected connection in "connect" ACL: Country is banned
2022-10-05 21:11:16 SMTP connection from [104.248.203.191]:54131 closed by DROP in ACL
2022-10-05 21:11:29 SMTP connection from [180.76.179.193]:33432 (TCP/IP connection count = 1)
2022-10-05 21:11:29 H=[180.76.179.193]:33432 rejected connection in "connect" ACL: Country is banned
2022-10-05 21:11:29 SMTP connection from [180.76.179.193]:33432 closed by DROP in ACL
2022-10-05 21:11:29 SMTP connection from [180.76.179.193]:33446 (TCP/IP connection count = 2)
2022-10-05 21:11:29 H=[180.76.179.193]:33446 rejected connection in "connect" ACL: Country is banned
2022-10-05 21:11:29 SMTP connection from [180.76.179.193]:33446 closed by DROP in ACL
2022-10-05 21:11:29 no host name found for IP address 180.76.179.193
2022-10-05 21:11:29 no host name found for IP address 180.76.179.193
2022-10-05 21:11:53 SMTP connection from [159.223.48.120]:44608 (TCP/IP connection count = 1)
2022-10-05 21:11:54 no host name found for IP address 159.223.48.120
2022-10-05 21:11:54 SMTP call from [159.223.48.120]:44608 dropped: too many unrecognized commands (last was "Connection: close")
2022-10-05 21:12:40 cwd=/etc/csf 2 args: /usr/sbin/exim -bpc
2022-10-05 21:13:58 SMTP connection from [43.157.18.137]:61736 (TCP/IP connection count = 1)
2022-10-05 21:13:58 H=[43.157.18.137]:61736 rejected connection in "connect" ACL: Country is banned
2022-10-05 21:13:58 SMTP connection from [43.157.18.137]:61736 closed by DROP in ACL
2022-10-05 21:13:58 no host name found for IP address 43.157.18.137
2022-10-05 21:15:19 SMTP connection from [186.193.230.60]:65115 (TCP/IP connection count = 1)
2022-10-05 21:15:22 H=[186.193.230.60]:65115 X=TLS1.2:ECDHE-RSA-AES256-GCM-SHA384:256 CV=no rejected connection in "connect" ACL: Country is banned
2022-10-05 21:15:22 SMTP connection from [186.193.230.60]:65115 closed by DROP in ACL






